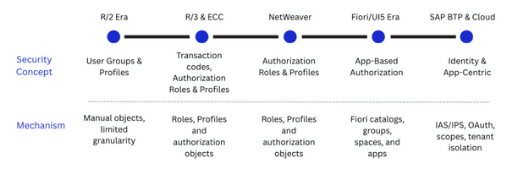
Over the past three decades, SAP has undergone a remarkable transformation—evolving from monolithic on-premises systems like R/2 and R/3 to the dynamic, cloud-native SAP Public Cloud solutions we see today. With this evolution, SAP security paradigms have been redefined—not just technologically but also philosophically. From rigid authorization profiles to flexible, app-based access control in the cloud, the journey of SAP Security reflects the broader shifts in enterprise IT architecture.
A Brief Evolution: From R/2 to SAP Public Cloud
SAP R/2, designed for mainframe environments in the 1980s, introduced centralized data processing with minimal security layers. When R/3 launched in the 1990s, client-server architecture revolutionized how businesses operated—but security was still largely perimeter-based, relying on trusted networks and internal firewalls.
As we moved into the 2000s, NetWeaver brought new integration capabilities, and authorization shifted from basic “profiles” to composite “roles” using the Profile Generator (PFCG). The focus was on transactional access, typically defined through TCodes and activity groups
Today, with SAP S/4HANA Public Cloud and Business Technology Platform (BTP), the security landscape has fundamentally changed. Perimeters no longer exist, users are global, systems are API-driven, and agility is paramount. Traditional SAP security principles simply do not suffice in this environment.
Traditional SAP Security: Role-Based and Perimeter-Dependent
| Principle | Description |
|---|---|
| Network trust | Users accessed SAP systems from secure, internal networks. |
| Role-based access control (RBAC) | Users were assigned roles built with authorizations for transactions. |
| Static authorizations | Roles rarely changed and were tightly controlled. |
| Segregation of Duties (SoD) | Focus on avoiding conflicting access. |
| Manual provisioning | Access requests were manually approved and provisioned. |
SAP Public Cloud Security: App-Centric, Dynamic, and Identity-First
Cloud deployments, particularly SAP S/4HANA Public Cloud and SAP BTP, introduced new expectations:
- Anywhere access from any device or location.
- App-based access control using Fiori apps, catalogs, and spaces.
- Identity-centric security integrated with IAS and IPS.
- Zero Trust Architecture and conditional access.
- API security and continuous compliance.
- Shared responsibility model with SAP.
From Profiles to Roles to Apps: How Authorization Design Evolved
Zero Trust and the Demise of the “Trusted Network”
In today’s cloud-first SAP landscape, the concept of a trusted internal network is obsolete. Zero Trust redefines security by assuming that no user, device, or system should be trusted by default—whether inside or outside the network. Every access request must be verified in real-time through identity validation, strict policy enforcement, and risk-based conditions. Least privilege access becomes the norm, ensuring users only get what they absolutely need. SAP supports this model through integration with Identity Providers (IdPs), Multi-Factor Authentication (MFA), and Just-In-Time (JIT) provisioning. Zero Trust isn’t just a framework—it’s essential for securing SAP in a hyper-connected, perimeter less world.
Key Differences: Traditional vs SAP Public Cloud Security
| Dimension | Traditional SAP Security | SAP Public Cloud Security |
|---|---|---|
| Access Definition | TCodes and roles (PFCG) | Apps, catalogs, spaces |
| User Provisioning | Manual (SU01/GRC) | Automated (IAS/IPS/IAG) |
| Perimeter | Internal, firewall protected | None – assumes untrusted networks |
| Authentication | Password-based | OAuth, MFA, SSO |
| Audit & Compliance | Periodic reviews | Real-time and automated |
| Threat Surface | SAP GUI and internal apps | Web UIs, APIs, partner systems |
| Change Management | Transport-based | CI/CD pipelines, config as code |
The Road Ahead: Future-Proofing SAP Security
Success in the SAP Public Cloud era demands a proactive security posture. Enterprises must adopt Zero Trust as the foundation—ensuring no user or system is trusted without verification. Automating user provisioning, policy enforcement, and compliance reporting is no longer optional—it’s critical for speed and accuracy. Teams must be upskilled in modern security concepts like OAuth, API governance, and Identity Access Management (IAM). Finally, organizations should invest in real-time monitoring and AI-powered platforms like ThreatSenseAI to detect, respond, and adapt to evolving threats instantly. In the cloud, security must be smart, scalable, and always-on.





